SOC Analyst Training by Experts
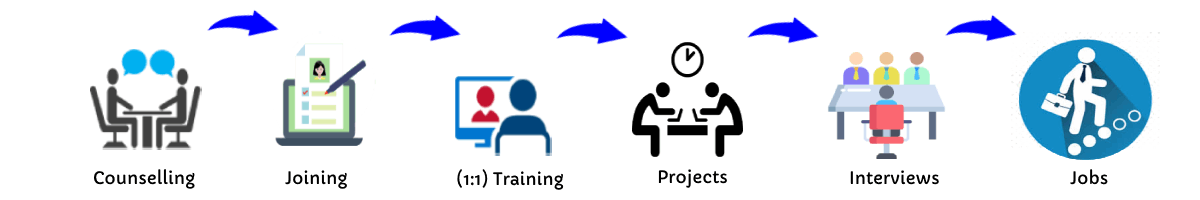
Our Training Process
SOC Analyst - Syllabus, Fees & Duration
Introduction to Cybersecurity
- Basics of cybersecurity
- Common cyber threats and attack vectors
Networking Fundamentals:
- Understanding TCP/IP
- Network protocols
- Firewalls, routers, and switches
Operating Systems
- In-depth knowledge of Windows, Linux, and possibly macOS
- File systems and permissions
Security Technologies
- Antivirus and anti-malware solutions
- Intrusion detection/prevention systems (IDS/IPS)
- Security information and event management (SIEM) systems
Incident Response
- Incident detection and analysis
- Incident classification and escalation
- Incident documentation and reporting
Threat Intelligence:
- Understanding threat intelligence
- Integrating threat intelligence into daily operations
Security Monitoring:
- Log analysis
- Network traffic analysis
- Endpoint security monitoring
Vulnerability Management
'- Identifying and prioritizing vulnerabilities
- Patch management
Security Policies and Compliance
- Understanding security policies and procedures
- Compliance standards and regulations
Hands-on Labs and Simulations
- Practical exercises & simulations for real scenarios
- Use of cybersecurity tools in a controlled environment
Soft Skills
- Communication and collaboration
- Analytical thinking and problem-solving
This syllabus is not final and can be customized as per needs/updates




 Vulnerability Assessment:Conduct regular vulnerability assessments to identify weaknesses in the organization's systems and networks. They need to stay updated on the latest cyber threats, security technologies, and industry best practices to effectively address the evolving landscape of cybersecurity risks. Some programs may be intensive, lasting a few weeks, while others may be part-time over several months. Their primary goal is to safeguard digital assets, sensitive information, and ensure the continuity of business operations. Utilize threat intelligence to proactively defend against emerging threats. Security Audits and Assessments:Conduct security audits and assessments to evaluate the effectiveness of security controls. Some programs may be intensive, lasting a few weeks, while others may be part-time over several months. Security Reporting:Generate and present regular reports on the organization's security posture to management and relevant stakeholders. The duration of SOC analyst training programs in Surrey can vary based on factors such as the depth of content, the training format (full-time, part-time, online, on-site), and the prior experience of participants.
What does a cyber security analysts do?
A cybersecurity analyst is a professional responsible for protecting an organization's computer systems and networks from security breaches and cyber threats.
Vulnerability Assessment:Conduct regular vulnerability assessments to identify weaknesses in the organization's systems and networks. They need to stay updated on the latest cyber threats, security technologies, and industry best practices to effectively address the evolving landscape of cybersecurity risks. Some programs may be intensive, lasting a few weeks, while others may be part-time over several months. Their primary goal is to safeguard digital assets, sensitive information, and ensure the continuity of business operations. Utilize threat intelligence to proactively defend against emerging threats. Security Audits and Assessments:Conduct security audits and assessments to evaluate the effectiveness of security controls. Some programs may be intensive, lasting a few weeks, while others may be part-time over several months. Security Reporting:Generate and present regular reports on the organization's security posture to management and relevant stakeholders. The duration of SOC analyst training programs in Surrey can vary based on factors such as the depth of content, the training format (full-time, part-time, online, on-site), and the prior experience of participants.
What does a cyber security analysts do?
A cybersecurity analyst is a professional responsible for protecting an organization's computer systems and networks from security breaches and cyber threats.



















































































